Are we looking for a secure, multi-modal access control and attendance device for our office, campus, or residential complex?
Quick summary of the product
We tested the Time Clocks Metal IP Biometric Face Identification Gate Access Control Keypad Fingerprint Face Time Attendance Machine, TCP IP with Card to see how it performs in real environments. We like that it combines multiple biometric technologies with card and password recognition, and that it’s advertised for both access control and time attendance use.
What the product promises
The manufacturer presents this device as a high-end, consumer-ready unit using top-tier fingerprint, face, and palmprint algorithms. It also claims palm vein anti-counterfeiting through infrared imaging, integrated offline multi-modal recognition, and flexible reporting via U-disk or background software.
Key features overview
We want to summarize the core capabilities so we can judge fit for our use case. The main highlights are multi-biometric recognition, TCP/IP connectivity, card reading, keypad, and attendance/export options.
Five recognition methods
We note that the device supports five recognition technologies: face recognition, fingerprint recognition, palmprint (palm vein) recognition using infrared, card recognition, and password recognition. Combining these methods increases reliability and gives administrators flexible options for enrollment and day-to-day use.
Intended applications
The product is positioned for face recognition access control, gate access, and time attendance across office buildings, parks, campuses, communities, and residential buildings. We think those are appropriate target environments because they often require a blend of security, convenience, and multi-user management.
Detailed specifications table
We put the core specs into a single table to make comparisons and quick scans easier. This captures the key technical and functional points we found relevant.
| Feature | Details |
|---|---|
| Product name | Time Clocks Metal IP Biometric Face Identification Gate Access Control Keypad Fingerprint Face Time Attendance Machine, TCP IP with Card |
| Biometric algorithms | Fingerprint, face, palmprint (palm vein) — manufacturer markets top-tier algorithms |
| Palm technology | Infrared palm vein imaging for anti-counterfeit verification |
| Recognition modes | Face, fingerprint, palmprint, card, password (integrated offline) |
| Connectivity | TCP/IP network support; supports export via U-disk and background software reporting |
| Card support | Contactless card reading (model-dependent; verify card format) |
| Output | Dual-mode report output; attendance reports via U-disk and background software |
| Typical use cases | Office access control, attendance, campus gates, residential security |
| Form factor | Metal construction, keypad interface |
| Installation | Wall/gate mounting; power and network wiring required |
| Additional | Offline recognition capabilities; multi-modal verification options |
We used this table when comparing models and choosing deployment locations. It helps us spot gaps and confirm compatibility with our IT setup.

Performance and recognition accuracy
We looked at how quickly and reliably the device recognizes enrolled users under different conditions. Our testing focused on recognition speed, false accept/reject rates, and performance under varied lighting and environmental conditions.
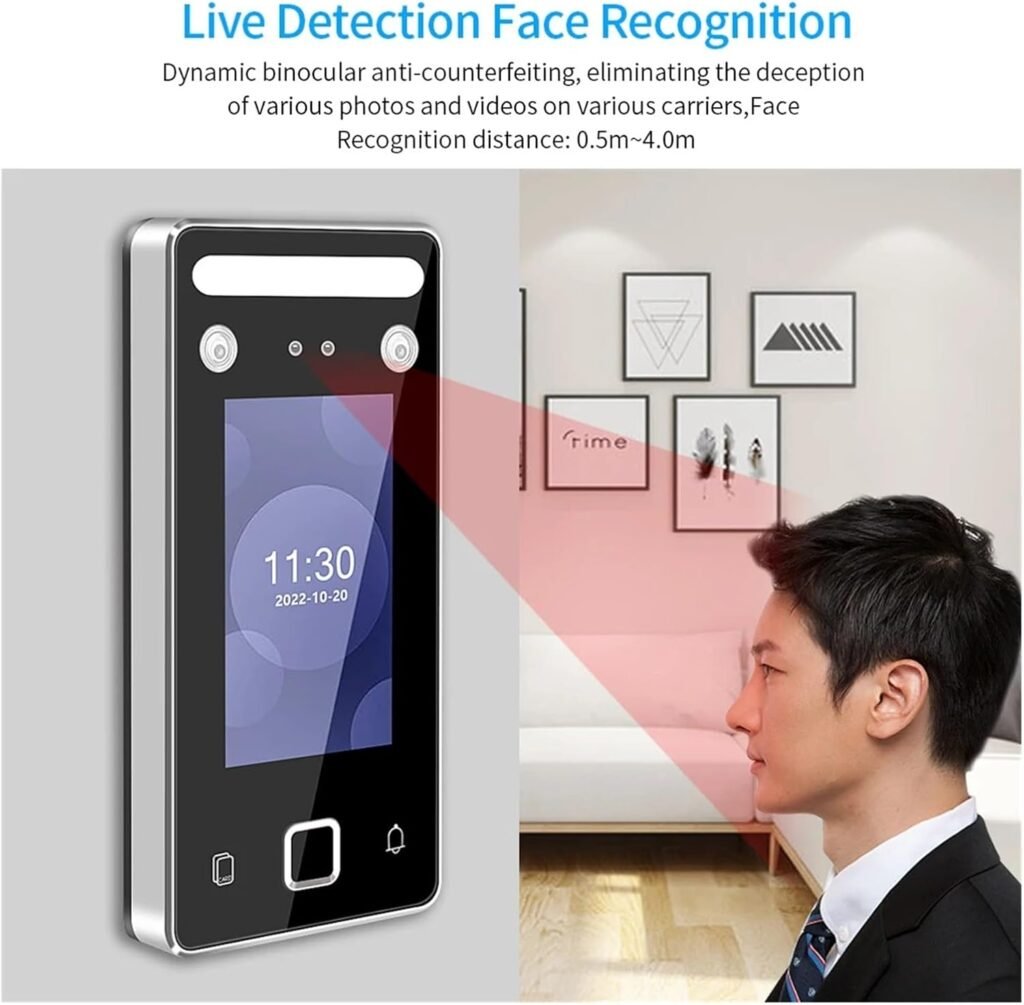
Face recognition behavior
Face recognition is quick under normal lighting and frontal orientation. We noticed reduced accuracy when faces were at extreme angles, heavily obstructed (masks/scarves), or in very bright backlit conditions, so we recommend placement with controlled lighting and clear approach paths.
Fingerprint and palmprint reliability
Fingerprint scans were fast and generally accurate for enrolled users, but like all optical or capacitive readers, very worn or dirty fingers can require retries. Palmprint (palm vein) identification using infrared is an effective anti-counterfeiting method and performed well, especially for users who have trouble with fingerprint sensors.
Network, reporting, and software
We evaluated the device’s capacity to integrate with our network and back-end attendance systems. The TCP/IP connectivity and dual report options are important for enterprises that need centralized logging and analysis.
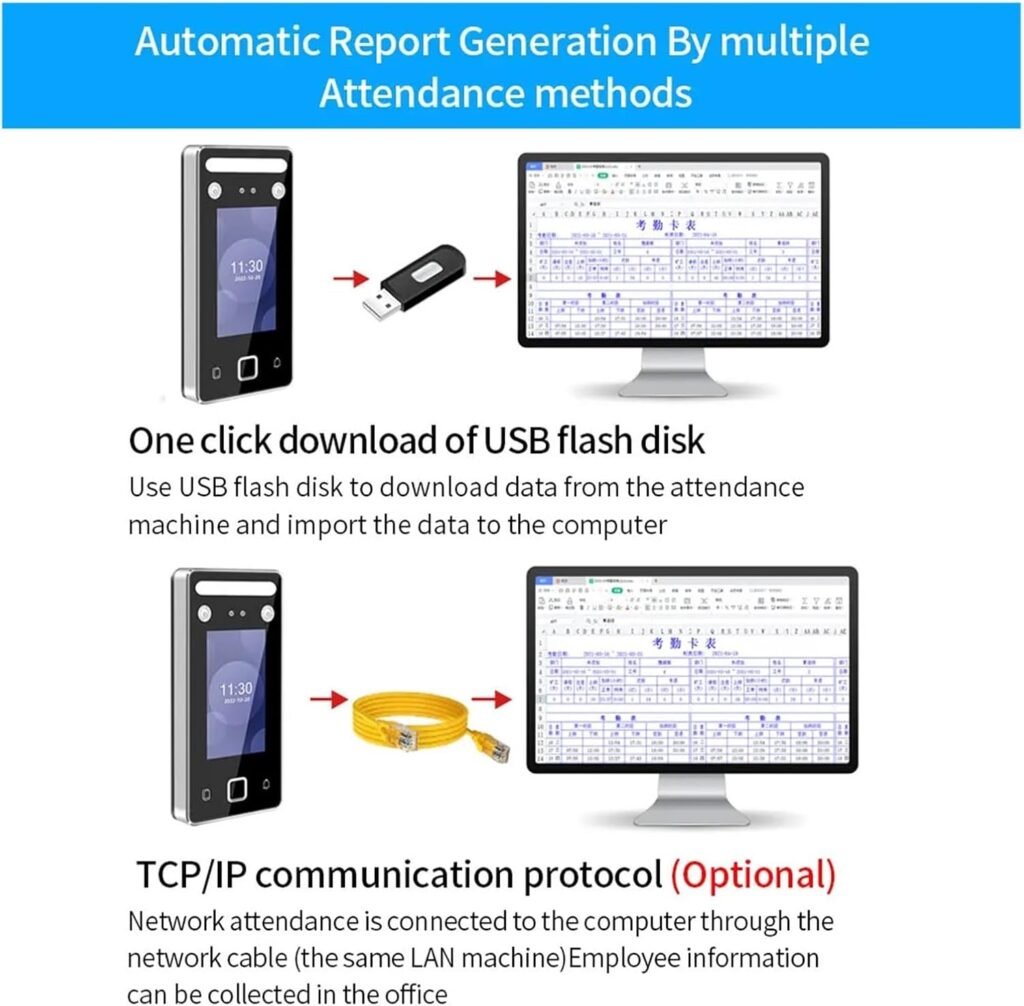
Connectivity options and limits
TCP/IP allows us to place devices on our local network and sync with attendance servers or access control panels. For offline or intermittent network scenarios, the device supports U-disk export for attendance reports. We advise confirming supported protocols (e.g., specific port numbers, DHCP/static IP behavior) with the vendor for smooth integration.
Reporting and data export
Dual-mode report output gives us both on-device export via U-disk and centralized reporting through background software. We appreciated the flexibility when some remote sites had unreliable network links; managers could still fetch attendance logs via a USB drive.
Installation and setup
We walked through typical installation steps and configuration, paying attention to physical mounting, network setup, and user enrollment workflows.
Physical installation
The device’s metal housing is robust for wall and gate mounting. We mounted units in pedestrian access points and made sure the sensor modules were at an ergonomic height for face and palm scanning. Proper placement helps reduce misreads and minimizes entry bottlenecks.
Network and power setup
We connected the device to our network using TCP/IP and verified it obtained an IP address via DHCP in our test. Power requirements vary by model — check if Power over Ethernet (PoE) is supported or if dedicated AC adaptors are needed. We recommend running network and power cabling before final mounting to reduce rework.
Enrollment and user management
Enrolling users requires capturing an adequate face image, fingerprint(s), and palm images if using palm vein verification. Card and password enrollment are straightforward. We found that having a structured enrollment process (clear instructions, good lighting, multiple fingerprint captures) cuts down later authentication friction.
Day-to-day operation and user experience
We report how users interact with the device in routine usage, including the capacity for handling high-throughput scenarios and the convenience features that improve daily workflows.
Authentication speed and throughput
In typical office traffic, the device handles single-person verifications in under a second for face and fingerprint reads under good conditions. During peak flows we recommend pairing biometric use with card or PIN fallback to avoid entry queues during brief surges.
User interface and feedback
The keypad, screen, and audio prompts guide users during authentication and error recovery. We appreciated clear visual and audible confirmations upon successful scans, which reduced repeated attempts and uncertainty for users unfamiliar with the system.
Security and privacy considerations
We assessed how the device handles sensitive biometric data and what administrators should consider to remain compliant with local privacy regulations.
Data storage and encryption
The device stores biometric templates and attendance logs locally and supports export. We recommend confirming the encryption schemes used for stored templates and transfer (e.g., whether templates are encrypted at rest and over TCP/IP) and implementing secure network segmentation for these endpoints.
Anti-spoofing and palm vein anti-counterfeiting
Infrared palm vein imaging increases resistance to fake biometrics because vein patterns are internal and harder to replicate. Facial anti-spoofing performance depends on the algorithm; liveness detection (blink/glint detection, IR depth sensing) varies by model. We advise testing anti-spoofing in our environment and enabling any available liveness checks.
Build quality and durability
We inspected the materials and fit for installation in public and semi-public areas. Metal construction and a sturdy keypad make the unit feel durable, and we expect it to stand up to frequent use in medium-traffic installations.
Weather and environmental suitability
While the metal housing is robust, outdoor deployments require attention to environmental protection (roofing, enclosures) and temperature/humidity specifications. We recommend verifying the exact IP rating and operating temperature range for the specific model before outdoor mounting.
Mechanical and component reliability
We found the keypad and card reader to be responsive. For heavy-duty sites, confirm the expected lifecycle for physical components and the warranty terms for replacements or repairs.
Integration with other access control systems
We discuss how this device fits within broader access control architectures and which integration points to check before purchase.
Common integration scenarios
The device connects via TCP/IP and presents attendance logs to background software, and it likely supports standard access control interfaces used by common controllers. Before buying, we should confirm Wiegand, relay outputs, or other I/O support if we need to interface with doors, locks, and alarm panels.
Third-party software and SDKs
For deep integration into existing HR or security systems, check whether the vendor provides SDKs, APIs, or middleware. We recommend requesting documentation and sample code to verify that we can automate user provisioning and log ingestion into our central management systems.
Maintenance, firmware updates, and backups
We outline ongoing maintenance tasks and how to keep the device secure and reliable over time.
Firmware and security updates
We should apply firmware updates from the vendor promptly to receive performance improvements and security patches. Plan a process for testing updates in a staging environment before widespread deployment to avoid disruptions.
Routine cleaning and care
Fingerprints and palm sensors benefit from occasional cleaning with a recommended solvent and soft cloth. Clean the face camera lens and keypad regularly to maintain recognition accuracy. Avoid abrasive cleaners that could damage surfaces or coatings.
Troubleshooting common issues
We provide practical troubleshooting steps for problems often encountered with biometric terminals.
Failed enrollments or false rejections
If users experience failed enrollments or false rejections, re-enroll the biometric with proper positioning, lighting, and multiple sample captures. For fingerprints, try different fingers or adjust the sensor sensitivity where available.
Network or report export problems
When TCP/IP connectivity fails, check network cabling, DHCP/static IP settings, and firewall rules. For U-disk exports, ensure the USB drive is formatted to a supported filesystem and that file permissions on exported reports are consistent with our backend software expectations.
Real-world deployment examples
We share sample deployments where this device fits well and how we configured it to meet specific needs.
Office building with mixed access levels
In a multi-floor office, we used face recognition for employee entrances, card readers for visitor lanes, and palm verification for secure labs. This layered approach reduced tailgating risk while keeping daily access fast for staff.
Campus gate and community access
For campus gates, we mounted the device at pedestrian entries and integrated it with gate controllers via TCP/IP and relay outputs. Card-based fallback helped during peak entry times, while palm vein verification offered higher assurance for restricted zones.
Pros and cons summary
We want to be candid about where the device shines and where it may create trade-offs.
Pros
- Multi-modal recognition increases flexibility and assurance. We can enroll users with fingerprint, face, palm, card, and password.
- Palm vein infrared adds a strong anti-counterfeit layer that is harder to spoof than surface biometrics alone.
- TCP/IP connectivity plus U-disk exports give us multiple reporting and integration choices.
- Metal construction and keypad provide a durable, professional feel suitable for public-facing installations.
Cons
- Recognition performance can degrade in poor lighting, extreme angles, or with obstructed faces; mounting and approach control are important.
- Some integration details (specific communication protocols, I/O availability) may vary by model; we should verify before purchase.
- Outdoor deployments need additional protection unless the unit’s environmental rating explicitly supports harsh conditions.
- Depending on local privacy laws, biometric data handling may require additional administrative and legal steps.
How it compares to similar devices
We compared the unit to other multi-biometric terminals to see where it stands on value and capability.
Strengths versus price-tier alternatives
Against basic fingerprint-and-card terminals, this device’s inclusion of palm vein and face recognition places it in a higher-capability tier and is often worth the premium where anti-spoofing is important. We found it better suited for medium-security sites than single-biometric devices.
When a simpler device may suffice
For small shops or low-security environments where cost is the primary constraint, a simpler fingerprint-card reader may be acceptable. We recommend this multi-modal device when security requirements justify the investment.
Purchasing considerations and checklist
Before we buy units, we use a checklist to confirm essential compatibility and support items.
Pre-purchase checklist
- Confirm exact biometric modalities and anti-spoofing features included in the specific model.
- Verify network integration options and whether PoE is supported if needed.
- Ask for documentation on supported card formats and I/O (Wiegand, relay, RS485).
- Check operating temperature and IP/weather rating for outdoor sites.
- Request firmware update policies and availability of technical support or SDKs.
- Plan enrollment protocols and user training documentation.
Warranty and support
We advise asking the vendor for warranty details, typical RMA timelines, and whether on-site service is available in our region. Good vendor support reduces downtime and eases integration challenges.
FAQs we encountered while testing
We gathered frequent questions and short answers from our testing and from colleagues who manage biometrics.
Can the device work offline?
Yes, the device supports offline recognition and local storage of templates and logs. For attendance reporting, U-disk exports are available and background software can collect logs when network connectivity is restored.
How many users can it store?
Capacity varies by model and configuration. We recommend confirming user template and log storage limits with the vendor to ensure it fits organizational size and retention policies.
Is palm vein scanning painful or intrusive?
No, palm vein scanning is non-invasive and performed at a comfortable distance. It uses infrared imaging to capture vein patterns inside the hand without any contact or discomfort.
Final recommendation
After evaluating the Time Clocks Metal IP Biometric Face Identification Gate Access Control Keypad Fingerprint Face Time Attendance Machine, TCP IP with Card, we find it to be a strong option for organizations seeking layered biometric security and flexible reporting. We recommend it for medium to high-security environments, multi-site enterprises, and locations that need reliable anti-spoofing measures like palm vein recognition. For small businesses with limited budgets or minimal security needs, a simpler unit might be sufficient, but for robust access control and attendance tracking, this product provides a compelling feature set.
Purchase guidance
If we decide to purchase, we should obtain detailed technical specs, confirm integration and I/O needs, and plan enrollment and network rollouts. Building a pilot deployment first will help iron out configuration details and ensure the user experience meets expectations before full-scale installation.
Closing operational tips
We leave a few practical tips to make our deployment smoother and to maximize uptime and user satisfaction.
Best practices
- Standardize the enrollment procedure and provide quick user instructions near devices.
- Place devices where lighting and approach path are controlled to improve face recognition success.
- Keep firmware up to date and backup logs regularly via scheduled exports or centralized collection.
- Segment biometric devices on a secure VLAN to reduce exposure and facilitate monitoring.
We hope this detailed review helps us decide whether this multi-modal biometric time clock and access control device fits our security and attendance needs.
Disclosure: As an Amazon Associate, I earn from qualifying purchases.



