?Could the Time Clock Metal IP Biometric Face Identification Gate Access Control Keypad Fingerprint Face Time Attendance Machine(TCP IP with Card) be the secure attendance and access device we need for our facility?
Product Overview: Time Clock Metal IP Biometric Face Identification Gate Access Control Keypad Fingerprint Face Time Attendance Machine(TCP IP with Card)
We find this device to be a comprehensive multi-modal biometric terminal that combines face, fingerprint, palmprint, palm vein, card, and password recognition into a single metal-bodied unit. The manufacturer positions it as a high-end but consumer-accessible solution that uses advanced algorithms and infrared palm vein imaging to resist spoofing and provide reliable attendance and access control. We appreciate that it supports TCP/IP connectivity and offline operation, giving us flexibility for varied network environments and deployment scales. Overall, it looks suited to organizations that need both high security and multiple verification options without requiring separate devices.
What the product claims
The product claims to adopt the world’s top fingerprint, face, and palmprint algorithms while adding palm vein anti-counterfeiting via infrared identification technology. It states that it integrates five recognition modes—face, fingerprint, palmprint, card, and password—plus offline face recognition and dual-mode report output for attendance reporting. We find these claims appealing because they promise reduced false acceptances and rejections while offering redundancy in identification methods. The inclusion of U-disk export and background software statistics suggests compatibility with both local and centralized attendance workflows.
Who this is for
We see this device fitting organizations that require robust access control and attendance tracking in environments such as office buildings, parks, campuses, communities, and residential buildings. Large enterprises, educational institutions, gated communities, and multi-tenant office complexes are good matches because they often need integrated access and attendance systems with high security and flexible reporting. Smaller businesses may also find value if they want a single, future-proof device that can scale and support different authentication modes. In short, it’s designed for mixed-use deployments where both convenience and anti-spoofing are priorities.
Key Features
We want to highlight the most important features that set this unit apart so we can quickly assess fit for our needs. These features combine hardware robustness, multi-modal biometrics, and practical data handling options for attendance and access control.
| Feature | Description | Benefit |
|---|---|---|
| Multi-modal Biometrics | Face, fingerprint, palmprint, palm vein (infrared), card, password | Provides redundancy and flexibility; users can authenticate with their preferred method |
| Top-tier Algorithms | Advanced face, fingerprint, and palmprint algorithms | Higher accuracy, faster recognition, and lower false accept/reject rates |
| Anti-counterfeiting Palm Vein | Infrared-based palm vein imaging for anti-spoofing | Strong resistance to fake biometric attacks |
| Offline Face Recognition | Local face recognition capabilities without need for constant network | Reliable operation during network outages |
| TCP/IP Connectivity | Standard network interface for integration with backend systems | Centralized monitoring and remote configuration |
| U-disk Export | Export of attendance reports via USB drive | Simple offline report retrieval when network access is limited |
| Dual-mode Reports | Supports both local and background software report generation | Flexible reporting workflow for admins |
| Metal Housing | Rugged metal construction for durability | Better physical security and longevity in public spaces |
| Card Support | Works with existing card systems (likely proximity or RFID) | Easy integration with legacy access cards |
| Keypad Support | On-device keypad for PIN entry | Backup authentication and user-friendly configuration |
We find this table useful because it condenses the primary capabilities and why each matters. It gives us a quick way to weigh trade-offs and plan deployment.

Hardware and Build Quality
We place a lot of importance on hardware quality for devices that will be used daily and exposed to public access points. The Time Clock Metal IP biometric terminal appears to be built with a durable metal housing that should withstand frequent use as well as the occasional physical impact.
Design and Materials
We note the metal construction contributes to a premium, robust feel and helps deter tampering and vandalism in communal areas. The housing likely improves heat dissipation compared to plastic enclosures, which can be beneficial for continuous operation under higher workloads. The unit typically mounts near gates or doors, so the metal design also communicates solidity and security to users and visitors. From an aesthetic perspective, the finish tends to be neutral and professional, which helps it blend into office lobbies and gate enclosures.
Durability and Installation
We expect the device to handle varying environmental conditions better than plastic alternatives, especially in controlled indoor areas or sheltered outdoor gates. Mounting options usually include wall and pedestal installations, and the metal case provides strong anchor points. We should still protect the device from direct exposure to rain and extreme temperatures unless the manufacturer specifies an outdoor IP rating. For power and network connections, standard screws and cable glands simplify installation, and the metal case helps keep internal components safe from physical tampering.
Biometric Technologies and Algorithms
We value biometric accuracy and spoof-resistance equally, since poor performance leads to user frustration while weak spoof-defenses create security gaps. This machine incorporates sophisticated algorithms across multiple biometric types, which we see as an advantage.
Face Recognition
We find the face recognition capability uses leading algorithms designed to recognize faces quickly under various angles and lighting conditions. The device is suitable for access control gates and attendance terminals, where users can be recognized from short distance without needing to touch the device. Built-in infrared sensors or IR-assisted cameras may improve performance in low-light environments and reduce rejection due to shadows. Offline face recognition means we can maintain operations even when network connectivity is interrupted.
Fingerprint Recognition
We observe that the fingerprint module leverages top-tier fingerprint algorithms, likely optimized for high throughput and low error rates. Touch-based fingerprint sensors still have an edge for speed and user familiarity, and they work well when hands are clean and dry. In contexts where hygiene or touch avoidance is needed, fingerprint use may reduce, but it remains a dependable alternative when face or palm recognition is not ideal. Fingerprint templates stored securely can be managed centrally or locally depending on our network setup.
Palmprint and Palm Vein
We appreciate that the device supports both palmprint and palm vein recognition, with palm vein imaging performed using infrared illumination. Palm vein verification offers a strong anti-counterfeiting layer because veins are internal features that are hard to replicate. Palmprint recognition adds an additional visible-pattern biometric that is useful when fingerprints are worn or when users prefer a non-facial alternative. Combining palmprint and palm vein significantly increases the overall robustness of the system against spoofing attempts.
Multi-modal Authentication
We see the inclusion of multiple biometric modes—face, fingerprint, palmprint, and palm vein—alongside card and password methods as a strong selling point because it allows for layered security strategies. We can configure fallback options (for example, if a face recognition fails, users may authenticate with fingerprint or a card) to minimize false rejections and reduce access delays. Multi-modal systems also help with diverse user populations where certain biometrics are less reliable due to occupation, age, or medical conditions.
Performance and Accuracy
We expect high accuracy due to the stated use of world-leading algorithms, but real-world performance always depends on enrollment quality, environmental factors, and user behavior. We look at speed, false acceptance rate (FAR), and false rejection rate (FRR) as primary metrics.
Recognition Speed
We find recognition speed is typically very good with modern algorithms, often returning a match result in under a second for face and fingerprint identification. For palm vein scanning, the process may be slightly longer but still quick, often within one to two seconds. Speed matters in high-traffic scenarios, so fast recognition minimizes bottlenecks at gates and entrance points. We recommend testing peak traffic flows in our environment to ensure the device keeps pace.
False Acceptance / Rejection Rates
We expect low FAR and FRR because of the advanced algorithms and multi-modal verification options. However, performance depends on proper enrollment and periodic re-enrollment if users’ appearance changes. For high-security areas, we may configure stricter thresholds that marginally increase FRR but lower FAR. We advise running a pilot phase to tune thresholds and balance convenience with security needs.
Environmental Performance
The device should perform well in typical indoor lighting and in lightly sheltered outdoor areas thanks to infrared assistance and robust sensors. Extreme sunlight, heavy rain, or high humidity may degrade performance, especially for camera- or touch-based modalities. We recommend installing the device under a canopy for outdoor gates and ensuring placement avoids direct sunlight facing the camera to reduce glare. Regular cleaning of fingerprint and palm sensor areas will also help maintain consistent performance.
Software, Integration, and Reporting
We want devices that integrate cleanly with our management systems and provide clear attendance reporting. This product includes features for both local and central report management, which increases flexibility.
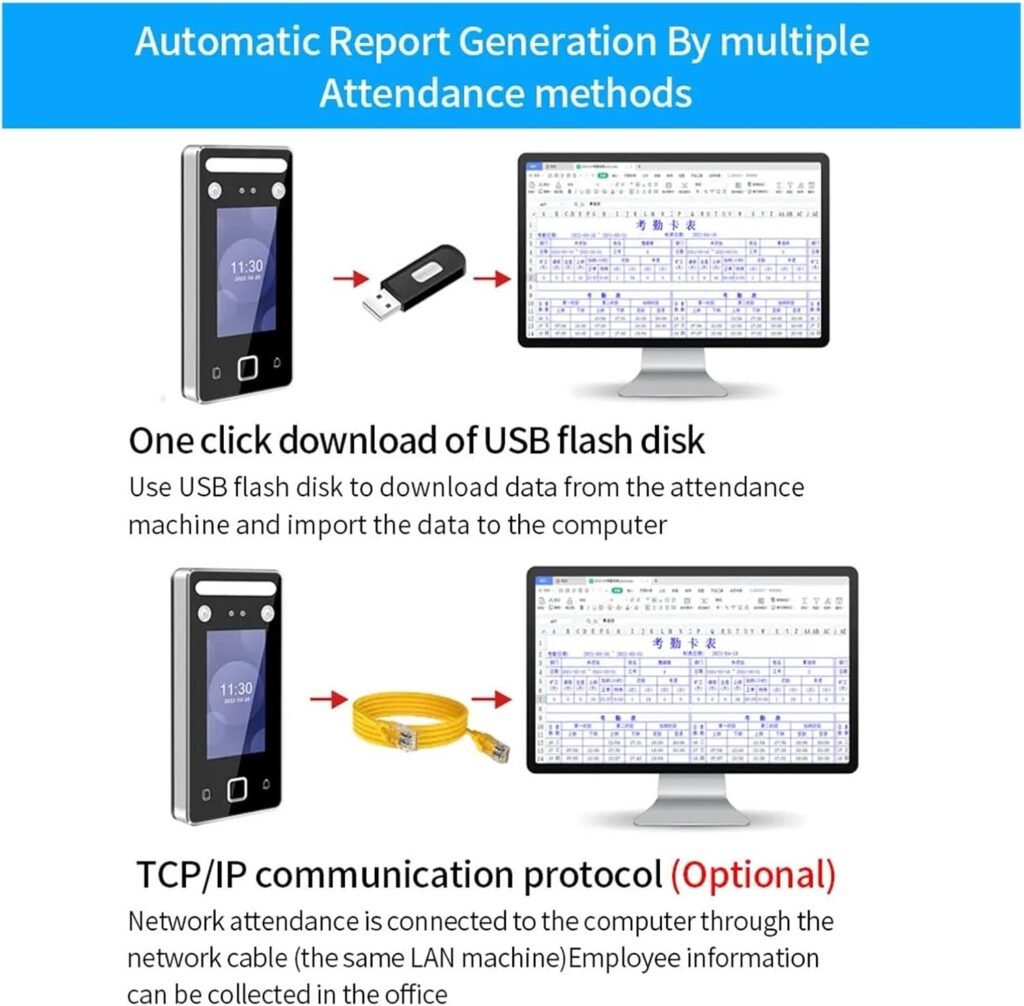
TCP/IP and Connectivity
We appreciate that the terminal supports TCP/IP connectivity, enabling real-time communication with backend attendance or access control systems. TCP/IP makes it possible to manage users, push firmware updates, and retrieve logs centrally, which saves administrative time. The device likely supports DHCP and static IP configurations, and may also offer optional protocols for integration with standard access control software. For secure environments, we should confirm if the device supports encrypted channels or VPN access.
Attendance Reporting and Export
We welcome dual-mode reporting: local export via U-disk and centralized reporting via background software. U-disk exports are convenient for small setups or backups, while centralized reports support HR workflows and longitudinal attendance analytics. The report formats usually include CSV or proprietary formats that the background software can parse into summaries, lateness metrics, and shift reports. We should confirm the supported file structures and how they map to our payroll or HR systems.
Background Software
The background software typically provides user management, device configuration, and attendance statistics. We find that a well-designed backend reduces manual work by automating shift rules, overtime calculations, and exception reporting. For larger deployments, server-based software allows us to manage multiple devices, track logs centrally, and maintain a single source of truth for user identities. We recommend verifying software compatibility, supported platforms, and any licensing requirements.
U Disk Export
We like that the device supports U-disk export, which allows us to retrieve attendance logs without connecting the device to the network. This is useful in remote locations or during network maintenance. Exporting via USB is straightforward and provides a quick backup path if centralized systems are temporarily unavailable. We should ensure the U-disk export format is compatible with our HR software to avoid manual conversion.

Security and Privacy
We take biometric data security seriously and expect devices to implement safeguards against spoofing, data leakage, and unauthorized access. This terminal includes several measures aimed at improving security posture.
Anti-spoofing and Anti-counterfeiting
We are reassured by the infrared palm vein capability and robust algorithms, both of which provide strong anti-spoofing resistance. Face and fingerprint modules may include liveness detection and challenge-response mechanisms to reduce the chance of being fooled by photos, videos, or fake fingerprint molds. Palm vein imaging, being an internal physiological characteristic, offers particularly strong resistance to external spoofing attempts. Still, we should test liveness detection on our specific device sample to validate manufacturer claims.
Data Storage and Encryption
We expect that templates and logs are stored in encrypted form on the device and during transit to central servers, but we recommend confirming the device’s specific encryption standards. AES-based encryption for local storage and TLS for network transmission are common best practices. We should also confirm how user templates are handled during deprovisioning to ensure biometric data is removed securely when employees leave.
Compliance Considerations
We must consider local privacy laws and biometric data regulations before deploying any biometric system. Many jurisdictions require informed consent, data minimization, secure storage, and defined retention policies for biometric information. We recommend consulting legal counsel or privacy officers to confirm compliance and to prepare notices or consent forms. The device’s support for encrypted storage and controlled export can assist with compliance but does not replace policy and process controls.
Installation and Setup
We prefer devices that are straightforward to install and configure, so we can reduce the time to operational readiness. The device’s metal housing and standard interfaces make installation predictable for facilities teams.
Mounting and Power
We recommend mounting the device at a comfortable height for users, typically on a reinforced wall or pedestal near the door or turnstile it will control. Power options usually include PoE (if supported) or DC power adaptors; we should confirm which is available on our model. Cable routing should be planned to protect against tampering and to meet aesthetic expectations. For outdoor or partially sheltered installations, we should add a protective hood or housing to prevent direct rain and sun exposure.
Network Configuration
The device’s TCP/IP support makes it versatile for networked installations. We should plan IP addressing, subnetting, and firewall rules in advance to ensure the device communicates with our backend securely. If we have VLAN segregation for security, we’ll place the device on a dedicated access control VLAN and ensure only necessary ports are open. For remote sites or intermittent connectivity, offline operation combined with periodic U-disk exports provides a fallback.
Enrollment Process
We find that proper user enrollment is critical to achieving the advertised performance. For face recognition, capturing multiple angles and expressions during enrollment reduces false rejections. For palm and fingerprint enrollment, clean hands and proper finger/palm placement yield better templates. We recommend a supervised enrollment session where technicians check sample quality and re-enroll as necessary. For large deployments, scheduling phased enrollments and providing simple instructions reduces confusion and speeds up adoption.
Usability and User Experience
Devices that are secure but cumbersome to use often end up being bypassed. We check for ease of use for both end users and administrators.
Interface and Keypad
We like that the unit includes a keypad for PIN input and likely a small display for user prompts and status messages. Clear prompts help users understand the required action, whether it’s placing their hand, presenting a card, or looking at the camera. A tactile keypad also provides resilience when touchscreens may be less desirable or in cold climates where gloved use is common. Administrators appreciate simple on-device menus for quick troubleshooting and user tests.
Training and Daily Use
We find that minimal user training is required for biometric operations if prompts are clear and enrollment is thorough. For visitors or occasional users, card or PIN fallback options help reduce friction. For daily users, the multi-modal approach increases the probability of a successful authentication on the first try, which reduces queues and friction. Periodic reminders to keep sensors clean and to re-enroll when appearance changes (such as new eyewear) help sustain long-term usability.
Use Cases and Deployment Scenarios
We consider where the device delivers the most value, given its multi-modal biometric capabilities and robust construction.
Office Buildings and Corporate Campuses
We think this product is well-suited to office buildings and corporate campuses where centralized attendance tracking and secure access control are essential. With TCP/IP integration, the device can feed HR and security systems in real time, support shift-based access rules, and maintain comprehensive logs for audits. The face recognition module is particularly useful in office lobbies where touchless access is preferred, and the metal build ensures a professional appearance.
Schools, Campuses, and Educational Institutions
We believe campuses and schools benefit from the multi-modal approach since students and staff vary widely in age and biometric suitability. For example, fingerprints may be unreliable for very young children, whereas face or card-based methods might be more practical. The ability to export attendance reports easily helps academic administrators with roll call records, while the palm vein feature enhances security in sensitive areas like laboratories.
Residential Buildings, Parks, and Communities
We find gated communities and residential complexes can use this device for secure access to common areas and building entrances. Palm vein and face recognition help reduce unauthorized access while card options support guests and service personnel. For parks and recreational areas with staff, the attendance module provides a straightforward way to log shifts without needing separate time clocks.
Pros and Cons
We aim to present a balanced view so we can make an informed decision.
Pros:
- We appreciate the comprehensive multi-modal biometrics that improve reliability and security.
- We value the metal construction for durability and tamper resistance.
- We like the infrared palm vein imaging for its strong anti-spoofing properties.
- We find TCP/IP connectivity and U-disk export flexible for various deployment scenarios.
- We note offline face recognition keeps operations running during network outages.
Cons:
- We are cautious that advanced features may require more initial setup and calibration to perform optimally.
- We recognize potential higher cost compared to single-modality devices, which may affect smaller budgets.
- We should verify claims about encryption and compliance support, as manufacturers’ defaults vary.
- We anticipate that outdoor deployments may need additional housings to protect the device against weather.
Comparison with Similar Products
We compare this unit conceptually with other biometric terminals to see where it stands.
What sets it apart
We believe the combination of face, fingerprint, palmprint, and palm vein, together with card and PIN options, positions this device above many single- or dual-modality terminals. The metal housing, infrared palm vein capability, and offline face recognition further distinguish it for environments where spoof-resistance and redundancy matter. The dual-mode reporting and U-disk export give administrators flexible options not always present in simpler devices.
Limitations vs competitors
We acknowledge that some competitors may offer enterprise-grade centralized management platforms with more polished analytics and mobile integrations, while others may have specific certifications for outdoor weatherproofing that this device may lack. Also, brand support, firmware update cadence, and integration documentation vary significantly among vendors, and these non-hardware differences can influence total cost of ownership and long-term satisfaction.
Maintenance and Troubleshooting
We prioritize straightforward maintenance and clear troubleshooting pathways to keep devices reliable.
Routine Maintenance
We recommend periodic cleaning of fingerprint and palm sensors with isopropyl alcohol and a soft cloth to remove oils and dirt that degrade performance. Camera lenses should be wiped gently to maintain clear images, and housing surfaces can be dusted to prevent buildup. We should also review logs regularly to detect any pattern of failed authentications that may signal the need for re-enrollment or firmware updates.
Common Issues and Fixes
We often see network configuration issues, which can be resolved by verifying IP settings, routes, and firewall rules. Recognition issues can usually be traced back to poor enrollment, dirty sensors, or lighting; re-enrolling users with better capture techniques typically fixes many false rejections. If lag or crashes occur, checking firmware versions and performing updates can resolve stability problems. For persistent hardware faults, we recommend contacting the vendor for warranty support or parts replacement.
Cost and Value Considerations
We evaluate cost not only by purchase price but by total lifecycle cost including installation, software licenses, maintenance, and support.
We consider that an upfront higher price is justified when the device reduces the need to purchase multiple devices for different modalities and when it lowers administrative overhead via centralized reporting. When planning budgets, we factor in potential costs for installation labor, protective housings for outdoor use, integration services, and any background software licenses. We also account for savings from reduced time theft, streamlined payroll processing, and improved security outcomes.
Final Recommendation
We recommend the Time Clock Metal IP Biometric Face Identification Gate Access Control Keypad Fingerprint Face Time Attendance Machine(TCP IP with Card) for organizations that need a versatile, secure, and durable access control and attendance terminal. We feel its multi-modal biometric capabilities, anti-spoofing features like infrared palm vein imaging, and flexible reporting options give it strong value for mid-size to large deployments and for sensitive applications where security is paramount. Before purchasing, we advise running a pilot, confirming encryption and compliance details, and verifying the device’s compatibility with our existing access and HR systems to ensure smooth deployment and long-term satisfaction.
Disclosure: As an Amazon Associate, I earn from qualifying purchases.



